
You’ve likely already been the target of a neighbor spoofing call — you just might not know it. This clever little trick has been on the rise since early 2016.
What is neighbor spoofing?
Neighbor spoofing is the method of masking a phone number with a local area code so victims will believe they recognize (or should recognize) the number and feel safer in picking up the call.
There’s legal spoofing — for example when a company contracts with a contact center and allows it to use the company's name and phone number on the caller ID — and there’s illegal illegal spoofing, when fraudsters purposely disguise their real numbers to fool the call recipient and prey on unsuspecting victims. Once these bad actors have your customers on the line, they’ll start in on their same, old, and tired attempts to trick them out of their hard-earned dollars.
This is a strategic shift in traditional spoofing. In classic spoofing, a scammer will copy the first 5 or 6 digits of a company’s phone number with the hope of successfully posing as a local business. This change in strategy suggests that spam blocking providers like Hiya are successfully predicting neighbor scam calls.
In response to effective anti-spam solutions, the scammers have attempted to continue the scam by switching to a less targeted strategy; by generalizing their approach, scammers hope they can go undetected and, therefore, keep the scam viable.
Unfortunately, the scammers are right—predicting if a call is a neighbor spoof is much harder with three digits, as opposed to the traditional six—but Hiya is up for the challenge.
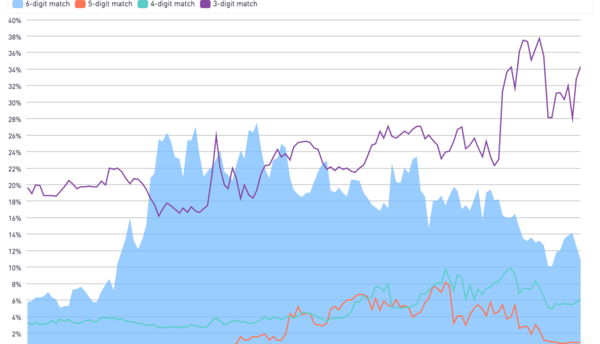
Hiya has aggregated and anonymized data to create algorithms that effectively, and efficiently, identify area code-based neighbor scams. Our model instantly recognizes if the number in question belongs to a scammer and blocks calls (or marks them as spam) to protect consumers. Conversely, the model also identifies calls from legitimate businesses and ensures that calls from that number aren't mistakenly flagged as spam.
It’s not just consumers—and Hiya—that recognize neighbor spoofing as a problem. The Federal Trade Commission (FTC) is also aware and has made steps to resolve it. In 2019, they began a major crackdown on robocalls and spoofing through a variety of regulations, which led to a major decline in neighbor spoofing.
Although it is impossible to completely stop phone spoofing, the decline shows that the FTC’s regulations initially made a substantial impact. However, in the last year, the number of neighbor calls have begun to rebound and even surpass their initial peak since the initial crackdown, as scammers have found ways around the new regulations, indicating that there is still lots of work to be done.
How to stop neighbor spoofing
Although it is difficult to completely block neighbor spoofing and prevent your company’s phone numbers from being spoofed, there are a few steps you can take to minimize risk for your company.
- Find a secure voice performance platform that provides visibility and control over any of your numbers that have been spoofed.
- Display a branded caller ID to consumers to give them the confidence to answer calls from you.
If you make more than 20,000 calls a month, see if any of your call center numbers have received negative (spam!) labels with a free Hiya Connect call inspection. Get additional information on how to stop your numbers from being spoofed with our How to Stop Spoofing eBook.

.jpg)

